
MOAB Puts a Bow on Data Privacy Week

Data breaches may seem like a dime a dozen, but this week brought something a little bit different: news of a massive breach of 26 billion record, by far the biggest ever recorded. The fact that the news of the Mother of All Breaches (MOAB) occurred during Data Privacy Week highlights the importance and the difficulty of keeping private data private in a super-connected world.
Word of the MOAB event came out of Cybernews, an online cybersecurity publication based in Lithuania. In a story posted January 24, Vilius Petkauskas, a deputy editor with the publication, described how Cybernews worked with Bob Dyachenko, cybersecurity researcher and owner of SecurityDiscovery.com, to uncover the breach.
The MOAB reportedly spans 12 TB across 3,800 folders, which were left unprotected on the Internet. The data appears to be comprised of previously compromised records, and there doesn’t appear to be any newly compromised data, Petkauskas writes. The haul includes data from millions of peoples’ LinkedIn, Twitter, Weibo, and Tencent accounts, among others.
The MOAB also sets the bar for a certain type of breach, dubbed a compilation of multiple breaches, or COMB. The researchers found “thousands of meticulously compiled and reindexed leaks, breaches, and privately sold databases,” Petkauskas writes. The fact that the data was previously disclosed doesn’t make it less critical.
“The dataset is extremely dangerous as threat actors could leverage the aggregated data for a wide range of attacks, including identity theft, sophisticated phishing schemes, targeted cyberattacks, and unauthorized access to personal and sensitive accounts,” Petkauskas quotes researchers as saying.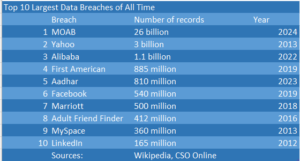
The MOAB dwarfs previous data breaches in size. It’s nearly 10 times bigger than the data breaches that impacted Yahoo customers in 2013, which the company didn’t disclose until years later.
The MOAB also caught the attention of data security professionals, including Doriel Abrahams, the principal technologist at Forter.
“Although the common assumption with this leak is there’s nothing ‘new,’ this COMB is extremely beneficial for bad actors,” Abrahams says. “Since they can leverage this data to validate whether users have similar or identical passwords across multiple platforms, they can attempt ATOs [account takeovers] on other sites not part of the current leak. Knowing which platforms users frequent is a superpower for social engineering scammers. They can be more targeted and, ultimately, effective.”
Richard Bird, Chief Security Officer at Traceable AI, wondered whether the new breach would spur companies and governments to take data security more seriously.
“Maybe it finally takes something like a MOAB to get the US Government and the companies that operate within its borders to wake the heck up,” Bird says. “We live in a nation with no national data privacy laws, no incentives for companies to be protectors of the data that they are trusted with, and no disincentives that seem to work. Companies will continue to trash the lives of their own customers by failing to protect the data that is associated with them and feel no pain for their failures. A list like this will only create more victims who will have to sort out the damages done to them on their own, with no consequences for the companies that gave that data away in the first place.”
As data breaches become more commonplace, there’s a risk that companies and individuals will become more blasé about them in the future. That could mean bigger breaches, more sensitive data, or both. For instance, 23andMe recently announced that hackers had obtained information about 6.9 million users who opted into the DNA Relatives feature.
Data Privacy Week is a great reminder that the onus for protecting customers’ personal data is on the companies that collect, use and share it, says Jennifer Mahoney, the manager of data governance, privacy and protection at Optiv.
“Companies have a responsibility to protect consumers, secure their data and do right by them morally, ethically and legally,” she writes. “Handling data privacy the right way drives consumer trust and builds long-lasting relationships.”
Technology innovation often outpaces legislation and regulation, Mahoney says. But that doesn’t mean that organizations should wait to be told by local, state, or federal laws how to handle data privacy. “They need to act now,” she says.
Artificial intelligence has surged in popularity thanks to new generative language models like GPT-4. However, GenAI raises the risk of data being abused, says Mark Sangster, the vice president and chief of strategy at Adlumin.
“Fundamental security practices should become the outer shield, with a specific focus on data and resulting obligations,” Sangster says. “In terms of artificial intelligence, companies need to protect data lakes and build policies and procedures to ensure private data does not mistakenly leak into data sets for large learning models that can easily expose confidential and potentially damaging information.”
It’s too easy to put a piece of data into a large language model without thinking about potential harms occurring downstream, says Jeff Barker, vice president of product at Synack
“As people look for shortcuts to do everything from writing emails to diagnosing patients, AI apps can now double as repositories of highly personal data,” Barker says. “Even if they don’t hold personal data from the outset, LLMs can still be poisoned through poor app security, resulting in a user sharing personal information with the adversary.”
GenAI poses a particular threat to data privacy, but there are many others, including the quantity and quality of the data stored, says Steve Stone, head of Rubrik Zero Labs. For instance, a typical organization’s data has grown 42% in just the last 18 months, growing to an average of 24 million sensitive records, he says.
“Breaches often compromise the holy trinity of sensitive data: personally identifiable information, financial records, and login credentials,” Stone says. “As long as these lucrative data types remain decentralized across various clouds, endpoints and systems not properly monitored, they will continue to entice, and reward increasingly sophisticated attackers.”
Biometric data, such as fingerprints and your face, are commonly touted as important enablers of higher security. But biometric data brings its own baggage as a particularly sensitive form of data, says Viktoria Ruubel, Managing Director of Digital Identity, Veriff.
“As consumers and employees, we have all seen or experienced biometric technology in action,” Ruubel says. “In business settings, face scans can enable entry into controlled access areas or even the office. However, while these tools have made identity verification easier and reduced some of the friction of identification and authentication, there’s growing concern around biometric data and privacy – biometric data is unique to each individual and permanent, making it one of the most personal forms of identification available.”
Data Privacy Day comes only once per year. But to truly enable data privacy, we must work at it every day, says Ajay Bhatia, global vice president and general manager of data compliance and governance at Veritas Technologies. “It’s a continual process that requires vigilance 24/7/365,” Bhatia says.
Related Items:
Buckle Up: It’s Time for 2024 Security Predictions
AI Regs a Moving Target in the US, But Keep an Eye on Europe
Feds Boost Cyber Spending as Security Threats to Data Proliferate

































