Microsoft and Intel Test Malware Protection Through Computer Vision

The world of malware protection has come a long way since the wild west of the early 2000s, when Trojans lurked behind every download. The malware threats that loom now are more advanced – and more evasive. Now, researchers from the Microsoft Threat Protection Intelligence Team are teaming up with Intel Labs to spearhead new, deep learning-based approaches for detecting and classifying malware.
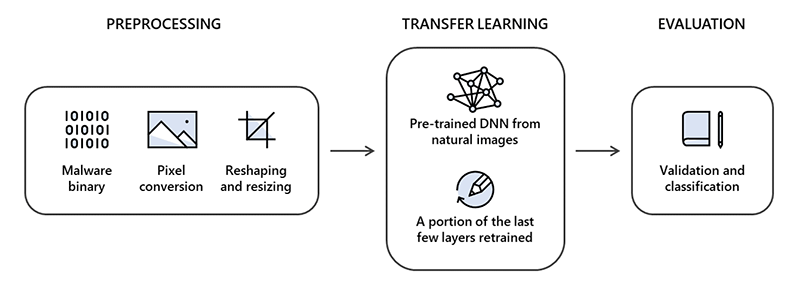
Specifically, the researchers examined the use of deep transfer learning from computer vision for static malware classification. Intel had already done work on that application of deep learning, so the researchers used that prior research and a real-world dataset from Microsoft to poke at an interesting idea: approaching malware classification as a computer vision problem.
The researchers were interested in the idea that the binary code of pieces of malware, if represented as grayscale plots, might exhibit patterns that could be automatically recognized as benign or malicious. To test this, they used static malware-as-image network analysis, or “STAMINA.” They broke the dataset – comprising 2.2 million portable executable file hashes – into three sections, with 60% used for training, 20% for validation, and 20% for testing.
“While static analysis is typically associated with traditional detection methods, it remains to be an important building block for AI-driven detection of malware,” wrote Jugal Parikh and Marc Marino for Microsoft’s Threat Protection Intelligence Team. “It is especially useful for pre-execution detection engines: static analysis disassembles code without having to run applications or monitor runtime behavior.”
The team found that STAMINA achieved high accuracy in malware detection with only a handful of false positives: at a 0.1% false positive rate, it attained 87.05% recall; at a 2.58% false positive rate, it attained 99.07% recall.
“The results certainly encourage the use of deep transfer learning for the purpose of malware classification,” Parikh and Marino wrote. “It helps accelerate training by bypassing the search for optimal hyperparameters and architecture searches, saving time and compute resources in the process.”
The researchers do acknowledge that there are cons to go along with the pros, however. While STAMINA is better at in-depth examinations of files, larger applications of the tool would likely begin to buckle under the computational weight inherent in converting billions of pixels into image files, lending an advantage to more traditional metadata-based methods.
Now, the researchers are working to advance another facet of deep learning for malware protection: optimizing deep learning models to be deployed on client machines for on-premises malware detection with low performance overhead.
To read more about STAMINA, click here.